How Much Does IoT Development Cost?
IoT, also known as the Internet of Things, refers to the billions of devices around the world that are connected to the internet. In a world that seems to be almost completely wireless, most physical objects can be used to collect and share data and transformed into an IoT device. In the previous article we have discussed the closely related topic on machine learning developer cost. And now we are going to explore the role of IoT and its cost, as IoT has quickly become a part of everyday life. Here’s how.
Role of IoT Developers in Everyday Life
It seems that almost every part of our everyday lives is controlled by some sort of digital connection. IoT is a term used for devices that have an internet connection and can communicate with the network they are associated without requiring human action to push a button. In your everyday life, IoT is involved than more than you may realize.
Here are some examples of everyday IoT:
- A light bulb that can be turned on and controlled through a smartphone app like the Philips Hue Bulbs
- A smart thermostat that allows you to control the temperature of your home or office from anywhere like the Nest Learning Thermostat
- A baby monitor that watches baby’s body position, breathing level, and body temperature like the Mimo Monitors
- Clothing such as the Polotech Shirt that records biometric readings like your heart rate and activity levels
- The Apple watch that allows you to track health and daily activities and even get notifications like e-mail and text message right to your wrist
The world of technology continues to evolve as we’ve moved from smart phones to smart cars. We could never have imagined years ago that we would be monitoring the temperature of our refrigerator through our cell phone or sitting back in a car that drives itself. Thus, such specialists as robotic process automation engineer and IoT Developers are growing in demand. And, as technology continues to change the way our lives work, there’s not telling where IoT is headed.
Demand of IoT Developer
While many areas of IT have an incredibly competitive job market, there seems to be a talent gap in the Internet of Things development field. In 2017 the industry had grown to over 2,500 companies employing nearly 342,000 people. As the demand for IoT developers continues to rise, the Internet of Things engineer salary has been reported to be the fastest growing in the industry.
According to recent research from Software.org, IoT has yet to reach its full potential because of the lack of skilled developers in the workforce. With United States universities graduating around 50,000 computer science students a year, the gap is obvious as the industry sees nearly 500,000 unfilled computing jobs.
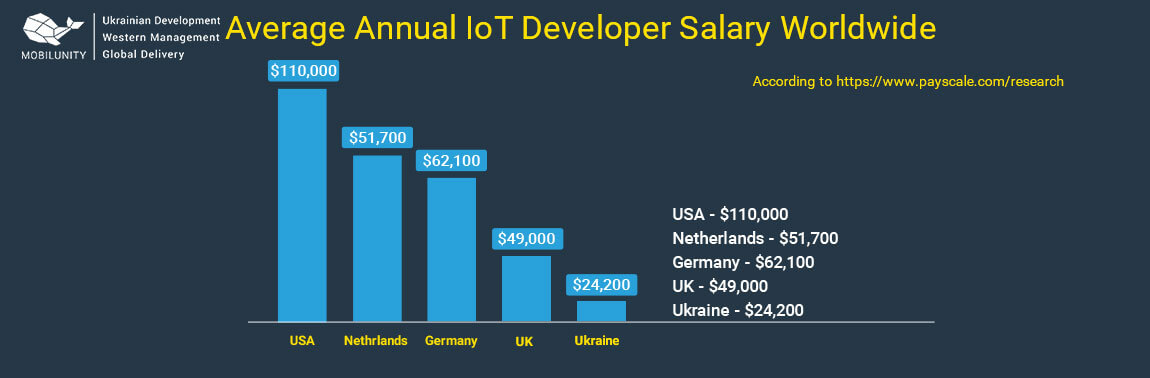
Internet of Things Engineer Salary
The IoT developer rate varies from country to country and even region to region within each country. In the United States, for example, the IoT developer salary California averages at $160,000 per year while the Internet of Things engineer salary Massachusetts averages at $106,000 per year. The average Internet of Things engineer salary in UK is annually $49,000, while the average annual salary in Germany is $62,100. In Ukraine, the average annual salary is $30,000*.
*Ukrainian salaries are provided based on Mobilunity’s Recruitment Team research on the local job markets. All salaries are net and do not include the service fee (in case of hiring on a dedicated team model). The salaries are provided for comparison purposes and could not be entirely accurate. Contact us to know the exact cost of hiring a developer corresponding to the required parameters.
Although choosing the most inexpensive developer does not always bring the best work, Ukrainian developers are some of the most skilled and competent professionals in the world. Mobilunity employs some of the best IoT dedicated developers in the business. If you want to hire IoT software engineers Mobilunity is the best option! Our dedicated IT professionals are skilled in a wide range of technologies that help create top quality results for your IT projects.
For the lowest IoT developer rates backed by high quality results, trust Mobilunity for your next IoT development project.
All salaries and prices mentioned within the article are approximate NET numbers based on the research done by our in-house Recruitment Team. Please use these numbers as a guide for comparison purposes only and feel free to use the contact form to inquire on the specific cost of the talent according to your vacancy requirements and chosen model of engagement.