5 Important Reasons to Hire Cyber Security Consultants
Almost a decade ago, cyber security consulting services may have sounded like something unusual and not much needed, nowadays a large number of businesses work with expert-level software security consultants to fine-tune their cybersecurity approaches and follow the best industry practices.
In this article, we will explore what cybersecurity consultants do, how they can help companies, and how to find the right expert for your business.
Who Is Cyber Security Consultant and Why Companies May Need One
The opportunities offered by the IT infrastructure carry both dependence and risks. With the development of IoT and digitalization of the vast majority of day-to-day operations, the threat of theft of the information and data, its damage, or substitution is also high.
According to the 2019 World Economic Forum report, hacker attacks and information leaks were identified as the most critical problems humanity faces, along with climate change and environmental issues.
A cybersecurity specialist is an expert that helps businesses to keep their data protected and confidential. Such a specialist searches end eliminates real and potential security threats, risks of data loss, as well as develops and implements measures to counter threats and solutions to protect against information loss. They can also handle the role of IT security consultant by developing and implementing the IT solutions needed, providing database migration consulting, and training the company’s employees on the best cybersecurity approaches.
With the automatization of all organizational processes, the need to prevent data loss and secure the system from potential threats is incredibly high. That is why these days, basically every company, whether a small startup or a large-scale corporation, needs the assistance of cybersecurity consultants to ensure a successful operation of the business and strong protection from any potential cyber attacks.
In most cases, having a cybersecurity specialist among employees is not enough, as they may not possess the necessary skills or be aware of the latest cybersecurity solutions. In-house cybersecurity experts can help to maintain the existing security approaches. Still, a lack of some knowledge may significantly impact the company’s performance in the long run, and that’s when a highly proficient cybersecurity consultant can help avoid potential problems and mitigate security risks.
Consultants in cybersecurity do not provide one-time package solutions, as each business requires a thorough assessment and tailored cybersecurity strategy. Top-level cyber security consultants will analyze the company’s needs, detect gaps in the workflow, and improve the processes. A cybersecurity consultant also helps companies keep up with the latest cybersecurity trends on the market and advise on the newest and most relevant protective software.
Increasing the security of your Microsoft Dynamics system is a critical reason to hire Microsoft Dynamics consultant, ensuring your business’s data and operations are safeguarded against cyber threats.
Here are 5 reasons why a company may need expert-level cybersecurity consulting services:
- Cyberattacks are becoming more severe and sophisticated, and hackers constantly look for new ways to bypass existing security algorithms.
- Without protection, every device connected to the network becomes vulnerable. Besides, you should be aware that hackers target not only systems but also people, so it is necessary to teach employees the basics of cybersecurity, and this is also the role of a software security consultant.
- A data breach can cost the business millions and even lead to bankruptcy. According to the IBM Cost of Data Breach 2020 report, the average damage from data breaches is estimated at $3.86M. And given the ingenuity of hackers and the increasing frequency of hacker attacks, security solutions are in greater demand than ever.
- Whether a company uses a private server or a cloud platform to run its business, most businesses require security protocols to keep communications and data transfers confidential. The more processes are handled in the cloud, the more is the need for highly effective cybersecurity solutions.
- Data breaches, system breaches, and identity thefts are often caused by low levels of cybersecurity awareness among employees. This leads to absurdity since all attempts and high-tech solutions implemented by a company go to waste because of one worker that neglects or doesn’t know cyber safety rules.
Understanding Responsibilities of Cyber Security Consultant
As the number of responsibilities and specter of knowledge of a cybersecurity specialist may vary depending on many factors, from the company’s size to the market it operates in; it’s vital to understand the main roles and responsibilities of a cybersecurity consultant:
- The main responsibilities of a cybersecurity consultant include a detailed analysis of the company’s cybersecurity risks and vulnerabilities, developing relevant cybersecurity protocols, and implementing relevant IT solutions. Such an expert can also assist with software updates, data protection, and maintenance practices.
- Cybersecurity consultants and freelance data engineer can also conduct training for employees on information security and cybersecurity issues, threats, and their consequences, to ensure that the cybersecurity maintenance protocols are not only developed but also appropriately followed.
- In large-scale organizations, a cybersecurity consultant has to develop a complex cybersecurity strategy covering all the potential cybersecurity threats and attacks and has mechanisms for their solving and prevention. Such a specialist must have a good understanding of the organizational structures and business processes in the given field, as well as the best practices for the given type of business.
When looking for well-versed cybersecurity consulting specialists and interviewing potential candidates, it’s crucial to identify whether the given expert will provide the quality of services needed. These questions may help you to conduct interview successfully and find out most of the important points before making an offer:
- How can you describe the cybersecurity practices that were in place in companies before you started working there?
- How can you describe the cybersecurity processes after you’ve implemented the changes?
- What were the biggest wins and losses in your cybersecurity practice?
- Do you have any previous experience working in this field and with companies of this size?
- What is your approach in training people that are not familiar with cybersecurity basics at all?
- How have the cybersecurity trends changed during the last year?
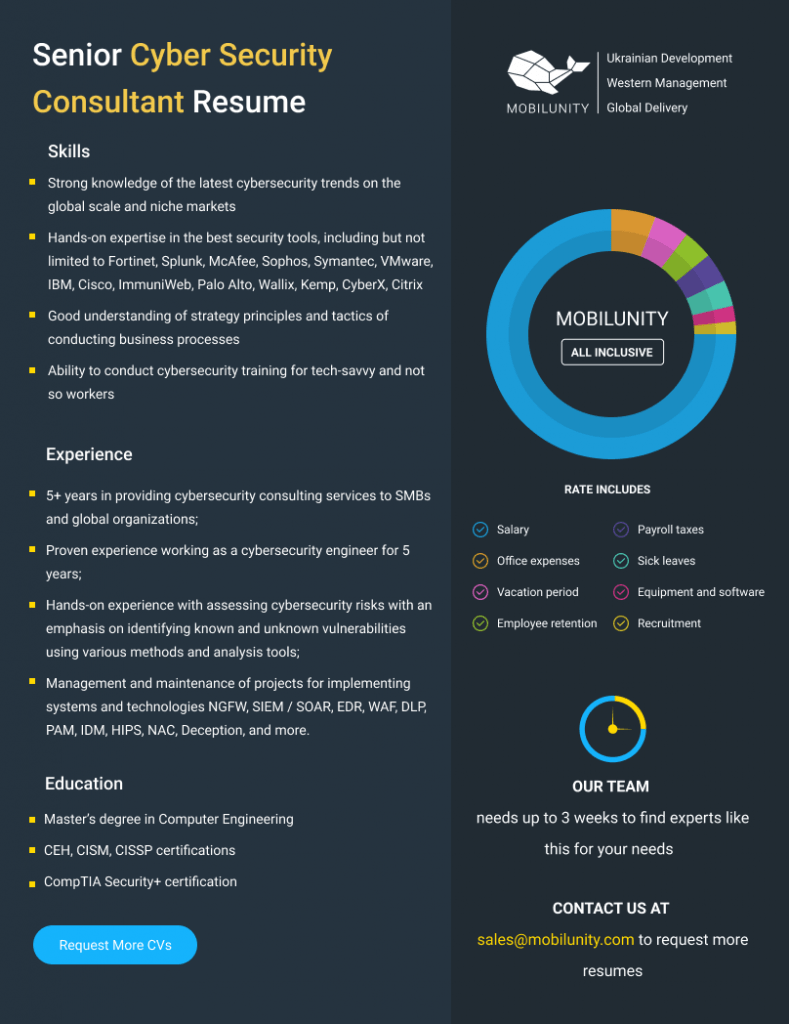
Senior Cyber Security Consultant Resume Example
When searching for a cybersecurity consultant, it’s vital to find a person that will fully meet your requirements and needs of the company. Below you can find a senior cyber security consultant resume example to learn more about the skills and experience to look for in an ideal candidate:
IT Security Consultants: What Exact Expert You Need?
With the increasing demand for different types of cybersecurity services and expertise needed, the branching of cybersecurity specialties grows as well. Depending on the company’s needs, it may be beneficial to hire a remote cybersecurity expert instead of an in-house one, or it may be more reasonable to work with an IT security consultant company.
If you need a concise guide on different cybersecurity specialties, we’ve listed the most in-demand cybersecurity experts below: that can be found down below:
- An application security engineer is responsible for secure app development, being engaged in the software development life cycle, from its design to product deployment and maintenance.
- A network security engineer can decide on and integrate protection tools to ensure the security of networks and servers, as well as control software configuration and provide database migration consulting.
- An information security analyst is responsible for setting up and continuously improving cybersecurity tools, performing penetration testing specialists, and monitoring business processes in terms of cybersecurity to ensure a well-protected environment.
- An IT security specialist works on the implementation and support of IT and informational infrastructure projects, as well as application services (may also take the role of a website security consultant).
- An IT security consultant can assess organizational processes, software, and network used to detect vulnerabilities and recommend the best cybersecurity approaches and solutions to keep the organization secure.
- A security architect is a specialist who assists in building and optimizing complex IT solutions to make them well-protected from possible cyber threats.
As you can see, the volume of work related to cybersecurity has grown and expanded so much that it requires an enormous amount of expertise, even in one field. Therefore, to ensure that you adhere to the latest and most effective cybersecurity practices, it’s best to opt for reliable cyber security consulting services.
However, depending on the roles and level of expertise of the given specialist, the IT cyber security consultant salary rates may vary greatly. Let’s take a look at the average salary costs of different cybersecurity consultants, based on SalaryExplorer statistics:
| Specialist | Average Salary, $ per hour | Hiring Difficulty |
| Application security engineer | $69/hour | Medium |
| Network security engineer | $55/hour | Low |
| Information security analyst | $58/hour | Medium |
| IT security specialist | $47/hour | Low |
| Security consultant | $59/hour | Medium |
| Security architect | $72/hour | Difficult |
Comparing Cyber Security Consultant Rates
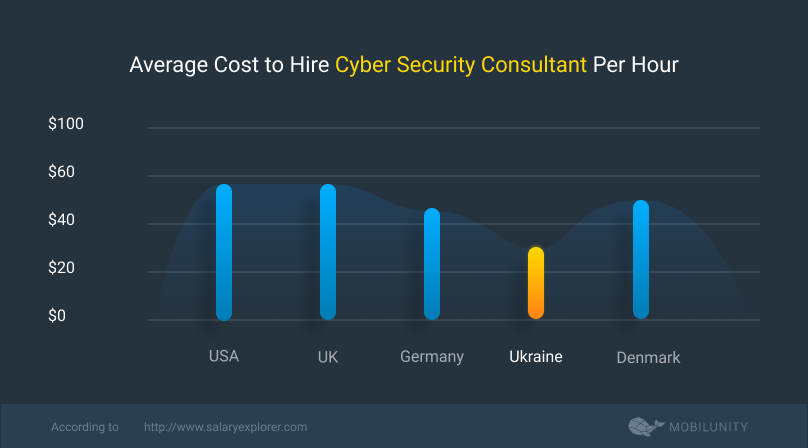
When analyzing a cyber security consultant resume example, you may wonder what are the main factors that influence the rates of such experts. Notably, it’s not an experience or certifications only that dictate the cost but also the location of the consulting specialist. Let’s compare an IT security consultant hourly rate in different countries, based on SalaryExplorer data and our Recruiting Team research over several local job portals:
- The US – $59/hour;
- The UK – £43/hour ($59/hour);
- Denmark – DKK 327/hour ($52/hour);
- Germany – €38/hour ($45/hour);
- Ukraine – $34/hour.
*Based on the data of our internal Recruiting Team
As you can see, Ukrainian specialists charge almost two times lower compared to American and European consultants. However, if you check a cyber security consultant resume of a Ukrainian cybersecurity expert, you will be impressed by their tech knowledge and vast experience in their field. That’s why many businesses want to hire highly qualified Ukrainian IT experts at a more affordable cost.
Exploring Ways of Hiring Cybersecurity Consulting Experts
When looking for cyber security consultants, there are three main work models for such experts. You may hire an IT consulting expert, cooperate with a freelance worker, or work with a dedicated remote cyber security consultant provided by a reliable IT resources provider. The choice solely depends on the need of your company, its size, and the complexity of the organizational structure.
Before settling on a working model, it’s crucial to consider both the benefits and downsides of each way:
| Advantages | Disadvantages | |
| Freelancer | Low price options for businesses on a budget Access to the global IT market talents Possibility to find the expert with specific experience Best if you need an expert for a one-time project or short-time cooperation | Lower liability for the contractors The least secure option, potential risks of data loss Low control over deadlines and work process |
| In-house | Ability to have an IT consultant at hand offline for smoother communication Higher accountability of the worker Full control over the work processes Ability to ensure the full security of the data | Large expenses for recruiting and retaining a highly-skilled expert Expenses for office supplies and software Expenses on constant training of the expert |
| IT outstaffing services | Comes as a cost-efficient option that is both affordable and reliable A mix of perks of having in-house teams and freelancers: accountability to hire the best talent on the global market and have a dedicated expert working as an in-house employee to pursue your company’s goals You still have the ability to monitor the work process and get detailed reporting No training, software, and organizational expenses | Possible timezone difference with the hired expert that may complicate the communication processes Other remote work challenges that can be overcome easily |
Mobilunity as Your Reliable Cyber Security Consultant Company
Mobilunity is a known Ukrainian outstaffing company that has been operating for 10+ years on the global market providing startups, SMBs, and large-scale organizations with dedicated development teams and top-level consulting services.
If you are in search of credible cyber security consultant firms that can help you find a personal cyber security consultant that will fully meet your business needs, our experts at Mobilunity know how to source and hire the best talents with the most relevant expertise in the field. Our clients note our high professionalism, fast solutions, and smooth cooperation.
To find a perfect remote IT security consultant for your company, we combine our own time-tested approaches with the latest industry practices:
- We discuss your business needs and create an ideal candidate profile.
- Then, we source potential experts according to the created cyber security consultant resume and select the best-matching ones for your review.
- Our recruiters conduct preliminary interviews with the candidates to make sure their skills and expertise match your business goals and organizational needs, so you receive a short list of the best talents.
- After you conduct interviews with the shortlisted experts, you can make an offer to the selected expert, and we negotiate the best offer conditions for your business.
Therefore, should you need professional cybersecurity consulting services, you can rely on Mobilunity in providing you with the right specialist for your business.
In search of professional-level IT security consultants? Find the right expert with Mobilunity!
All salaries and prices mentioned within the article are approximate NET numbers based on the research done by our in-house Recruitment Team. Please use these numbers as a guide for comparison purposes only and feel free to use the contact form to inquire on the specific cost of the talent according to your vacancy requirements and chosen model of engagement.