Trusted Penetration Testing Services Provider in Ukraine

- How Can Penetration Testing Save a Company?
- Types of Web Application Penetration Testing
- Advantages and Disadvantages of Penetration Testing
- How Penetration Testing Works
- Typical Tools Used by Pen Testers
- Penetration Tester Job Outlook
- Pentester Salary Worldwide
- Penetration Tester Interview Questions
- Mobilunity – Your Cyber Security Partner
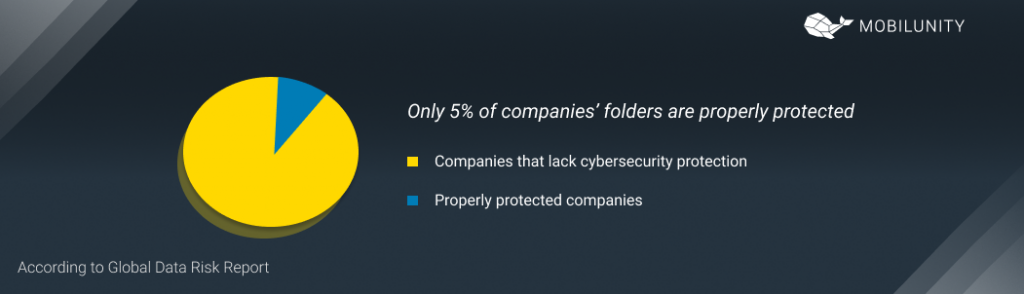
The number of cyber threats and attacks grows every day. The year 2020 made a new record when it comes to data breaches and cyber-attacks. To make matters worse, according to the Global Data Risk Report only 5% of companies’ folders are properly protected. About 78% of IT security specialists think that companies lack the proper protection against cyber attacks.
So how can a business secure itself and be more protected when it comes to sensitive data? This is where penetration testing services come into place.
Cyber security penetration testing is a comprehensive analysis of vulnerabilities and attack simulations to find the weak spots of web applications and company’s data. It allows getting a deep insight into the existing security system, its effectiveness, and the possible advancement measures. A web penetration tester does a targeted protection system assessment to check the general security of software or network.
A web penetration tester is also known as an ethical hacker. Such professionals run both automated testing, as well as intelligence gathering, and design simulations of attacks to penetrate the system and exploit its vulnerabilities. Pentesting services can be done in two directions, such as:
- Vulnerability assessment – automated scanning to find all the weak spots of the system. Information security consultant also suggests advanced protection measures.
- Simulated targeted attacks – in such a case, a web security tester creates scenarios and cases to test the most vulnerable or valuable assets of a company. It includes designing and executing aimed attacks on the network.
How Can Penetration Testing Save a Company?
Web application penetration testing is a crucial maintenance step for any company that deals with sensitive data. Whether one needs to test a new web application or existing security, system, pentesting can save a company in several ways:
- Find and resolve any vulnerability issues.
- Address growing and new cyber threats before any attack takes place.
- Increase efficiency of protection system.
- Train staff to act efficiently during attacks.
- Ensuring that all sensitive data is secured and properly protected.
Overall, it is a proactive measure to eliminate security risks. It is always better to act before an event happens, as data breaches and cyber attacks can be detrimental to a company’s functioning, finances, and reputation.
Types of Web Application Penetration Testing
As mentioned above, pen testing can be done in terms of vulnerability assessment or simulation of attacks. But those are not the only types of identifying application penetration testing methods. Here are the major types to keep in mind when looking for IT security consulting firms or pen testing service providers:
Internal Testing
This type of testing is done internally, within the organization’s LAN. It also helps to assess intranet web applications and databases. The main goal is to find any weak spots within the business’ firewall. It is essential because a lot of companies think that external security is much more important. As a result, they may miss a lot of vulnerabilities.
The internal system also has to be secured as there are many cases of malicious employee attacks (contractors, former employees, third parties, etc). Also, cyber threats can be presented in terms of social engineering or phishing attacks.
External Testing
In this case, an application penetration tester is focused on attacks happening outside the business. Mostly it is used for testing web applications and solutions hosted on the internet. It is crucial to test server and firewall security as well as IDS.
This is where ethical hacking comes into place. Testers do not have any information about the internal system. Their task is to target the system only by giving them an IP address. Testers look for information online and use penetration testing tools to find all necessary data for an attack. It can happen in several methods:
- Blind testing – a tester has only a name of a company. The job is to penetrate the system and give security insight into a real-life cyber-attack.
- Double-blind testing– in this case, the security team of the company has no idea that the test is happening. It helps to evaluate procedures and responses to a breach or attack.
- Targeted testing – both parties, an ethical hacker and security team are aware of the simulation. They work together and keep each other posted about their actions. It is a training exercise to get access to the hacker’s point of view.
Advantages and Disadvantages of Penetration Testing
Now, let’s define the pros and cons of penetration testing. Starting with advantages:
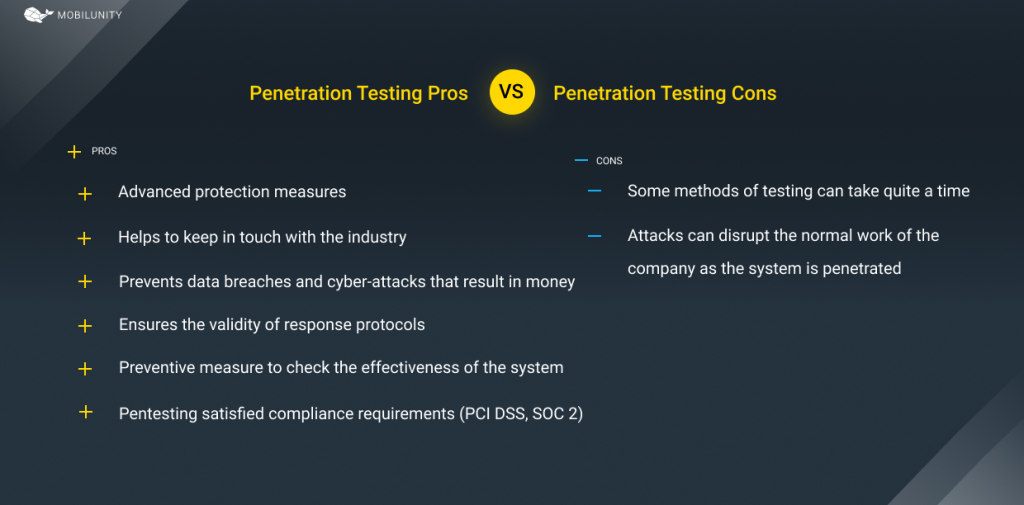
- Pentesting allows finding all weaknesses of the system and advancing protections measures accordingly.
- When done regularly, it helps to keep in touch with the industry and eliminate any new arising threats and risks.
- It helps to prevent data breaches or cyber-attacks that result in money, data, and reputation losses.
- Simulations allow training security staff in real-life circumstances. It ensures the validity of response protocols and helps to address any issue in the minimum time.
- It is a crucial preventive and proactive measure to check the effectiveness of the system, security of web application, or internal system.
- Pentesting satisfied some compliance requirements (PCI DSS, SOC 2). These security auditing procedures are necessary for many businesses.
So what disadvantages can such services have? Well, there are some concerns to keep in mind:
- Depending on the type and methods of testing, it can take quite a time, up to several months to do.
- Simulation of attacks can disrupt the normal work of the company as the system is penetrated. One needs to remember that such a possibility exists.
How Penetration Testing Works
Whether it is Azure or AWS penetration testing, the cycle is always the same. A professional remote penetration tester follows the exact steps to make sure everything is covered.
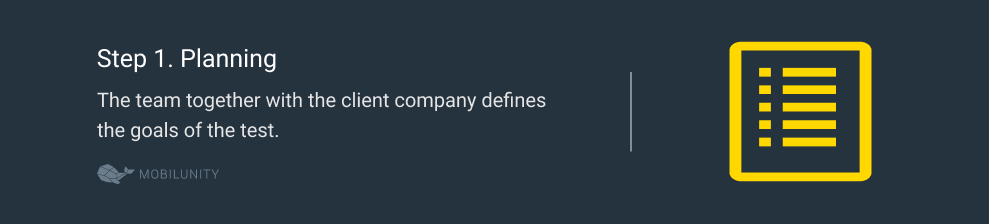
Step 1. Planning
At this stage, the team together with the client company defines the goals of the test. They can name specific systems to test, identify the most valuable assets, and decide on the methods to use.
Also, here is when intelligence gathering happens. If it is an internal test, programmers get access to LAN, collect network and domain names, etc. If it is an external test, they are only given an IP address or the name of the business and gather intelligence on their own.
Step 2. Scanning
Now it is time to scan the target network/application and figure out how it responds to different threats. Static analysis means evaluating the code and estimating how it acts in general. Dynamic analysis means scanning the code while it’s running.
Step 3. Attacking
As all the intelligence is gathered, testers can now gain access to the system or simulate cyber attacks. They use different types of threat modeling, like SQL injection or backdoors to evaluate all vulnerabilities. Programmers also try to exploit them as much as possible. This allows evaluating how much damage can be done and what potential risks are.
Step 4. Maintaining access
The next step is to maintain access to the app or system for as long as possible. In this case, testers know whether a weakness can be used for a persistent presence to access the sensitive data.
Step 5. Analysis and recommendations
All the results are presented in the form of a comprehensive report. It shows all the vulnerabilities and how they were exploited, as well as what data was stolen.
This data is used to give recommendations on advanced security measures, WAF settings, or other options to patch the protection system.
Typical Tools Used by Pen Testers
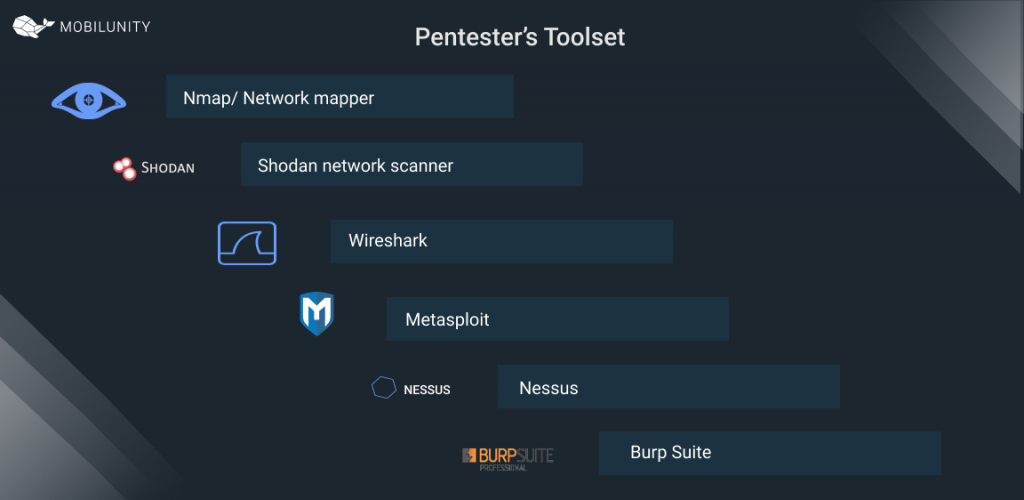
Although every case is different and requires a unique approach, here are the best pentesting tools that are commonly used by professionals.
- Nmap/ Network mapper gives data on the scripting language of an app. It also reveals the OS of the server, as well as its version and software used.
- Shodan network scanner shows publicly accessible data, such as server geolocation, software, and a number of open ports.
- Wireshark is a network protocol analysis tool.
- Metasploit is a testing tool for a framework that can find, select, and target a vulnerability.
- Nessus is a great vulnerability scanner that shows configuration issues as well as any malware present in the system.
- Burp Suite is an all-in-one tool for professionals working with web app security. It can be used on every stage of the pentesting cycle.
Penetration Tester Job Outlook
A penetration tester salary depends not only on the skills and experience but also on the popularity of this position. The employment for pen testers is projected to grow by 31% in 2019-2029, which is much higher than the average.
The responsibilities of a pen tester or ethical hacker include:
- Collect and analyze open-source data on the company and their system;
- Provide system assessment and detection of vulnerabilities;
- Testing the defensive mechanism of a business with static and dynamic analysis;
- Development of scripts and tools for such evaluation;
- Design and execute social engineering testing;
- Design and execute penetration simulations;
- Holistic analysis of received data and identification of the root of a problem;
- Provision of recommendations on resolving these issues.
An excellent penetration tester resume is also filled with a specific set of skills necessary for this job:
- Hard skills include knowledge of different OS, programming languages like Python, Golang, Bash, or Powershell. And knowledge of pen testing tools like Burp Suite, Wireshark, Nessus, Metasploit, etc.
- Soft skills include problem-solving, creativity, resourcefulness, and analytical thinking.
Also, excellent professionals need to have specific qualifications. They depend on the level of expertise, from junior to senior specialists. But usually, such an expert needs a Bachelor’s degree in Information Security or Computer Science. Advanced positions may require MA.
There are also some international certifications to look for, such as IEEE, OSCP, SANS, or GIAC.
When it comes to a pentester resume, the exact details also depend on the expertise level. Here are two resumes to compare – for middle and senior-level positions.
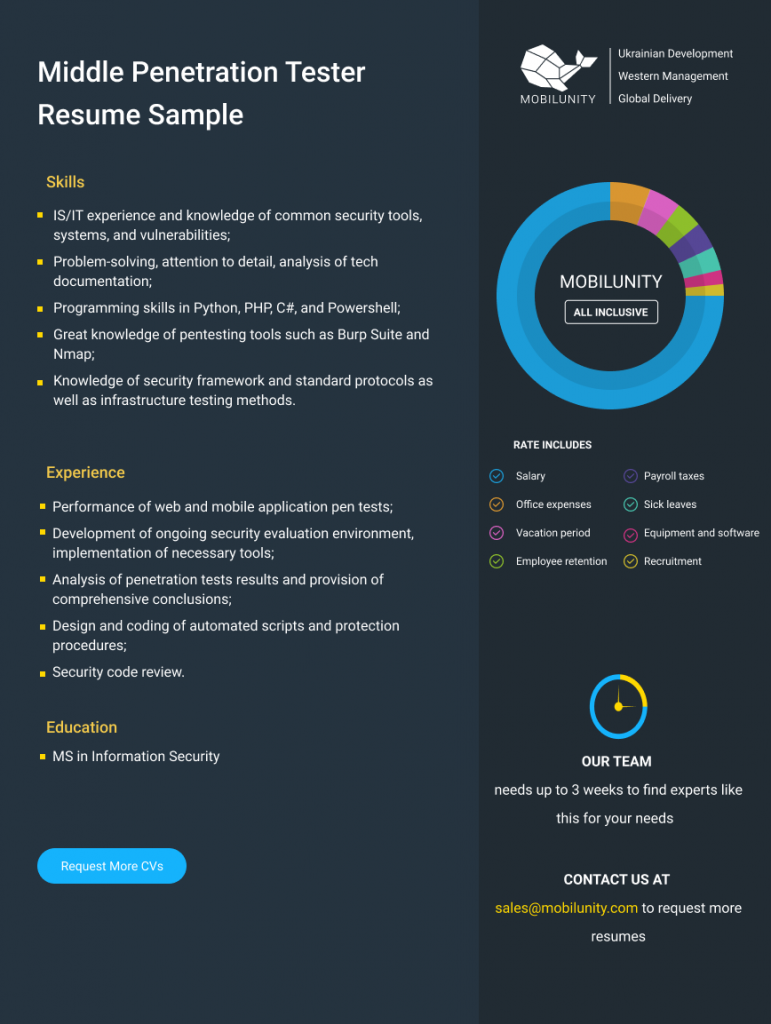
Middle Penetration Tester Resume Sample
Senior Penetration Tester Resume Sample
Pentester Salary Worldwide
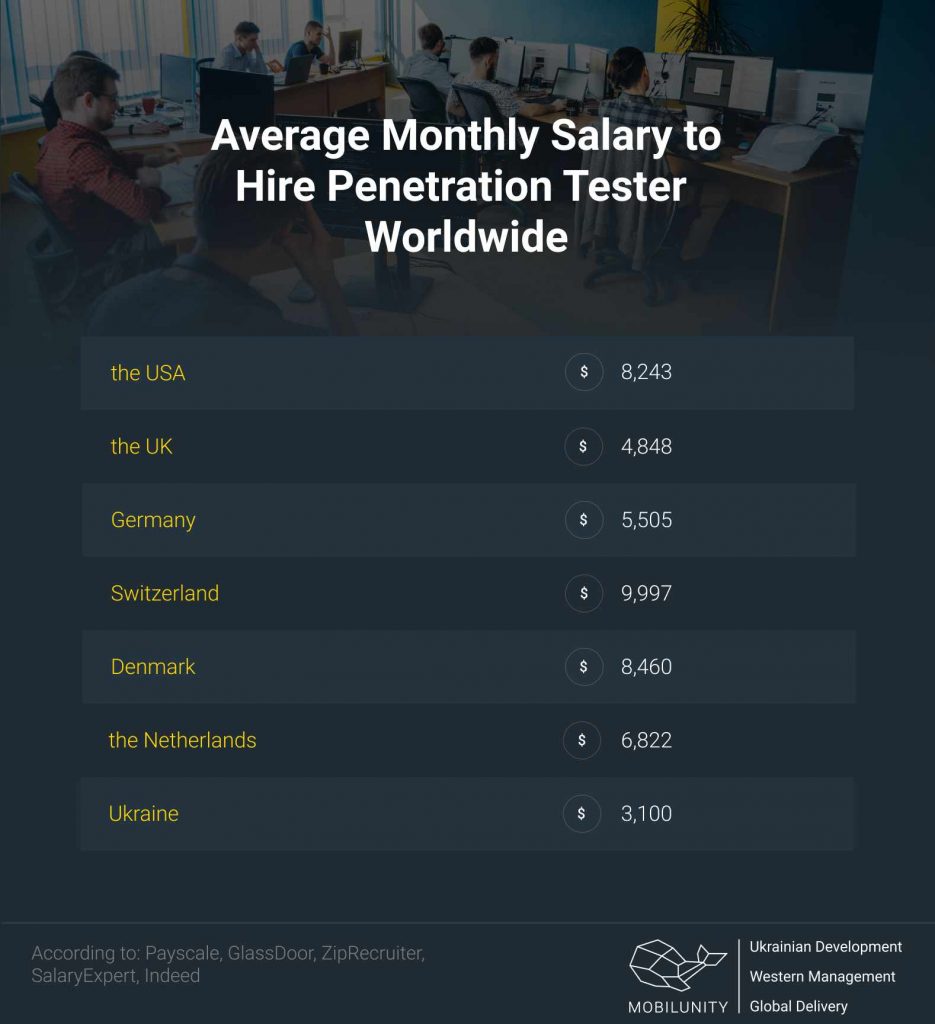
Of course, a senior penetration tester salary will be different from a junior specialist. But it is not the only factor to consider when estimating rates. Another essential contributor is the country of location, as outsourcing and remote hire is extremely popular. Here are monthly average rates for pentesters in different countries to compare:
- the USA – $8,243
- the UK – $4,848
- Germany – $5,505
- Switzerland – $9,997
- Denmark – $8,460
- the Netherlands – $6,822
- Ukraine – $3,100*
*Ukrainian salaries are provided based on Mobilunity’s Recruitment Team research on the local job markets. All salaries are net and do not include the service fee (in the case of hiring on a dedicated team model). The salaries are provided for comparison purposes and could not be entirely accurate. Contact us to know the exact cost of hiring a developer corresponding to the required parameters.
Penetration Tester Interview Questions
When looking for a professional, it is important to evaluate their expertise. Here are some questions to ask a penetration security specialist.
- What are the strengths and weaknesses of Linux and Windows in terms of security?
- What are the common methods to add security to a website?
- How to avoid brute force hacks?
- Can you explain the difference between symmetric and asymmetric encryption?
- How can sensitive data be protected during and after pen testing?
Mobilunity – Your Cyber Security Partner
Partnering with a dedicated dev team provider is an excellent choice when it comes to finding the right IT specialists. It allows saving money while hiring top-notch professionals to do the job. That’s why Mobilunity helps international businesses and companies to find top-notch programmers, consultants, and testers in Ukraine.
Mobilunity is a Ukrainian IT staff augmentation company with more than 10 years of experience. We’ve already helped more than 40 businesses from all over the world, including XPLG (Israel), ServIT (Sweden), Opportunity Network (UK), Minedia (Japan), and ICUC (Canada).
Mobilunity is a guaranteed partner in smooth and effective remote hires. We are ready to find the best penetration testers for your business to ensure the best digital protection for your assets.
Looking for a web penetration tester in Ukraine? Contact us now!
Disclaimer: All salaries and prices mentioned within the article are approximate numbers based on the research done by our in-house Marketing Research Team. Please use these numbers as a reference for comparison only. Feel free to use the contact form to inquire on the specific cost of the talent according to your vacancy requirements and chosen model of engagement.