Protect Your Business with Cyber Security Consulting Services
- What Cyber Security Consulting Is About?
- Main Types of Cybersecurity Threats
- Services of Cybersecurity Consulting Companies
- The Role and Responsibilities of Cybersecurity Consultant
- List of Questions to Evaluate Whether You Need a Cybersecurity Consultant
- A Perfect Cybersecurity Consulting Firm
- Mobilunity – Excellent Ukrainian Vendor
Cybersecurity is an extremely important issue to representatives of all industries. Whether it is a tech company, a bank, a pharmaceutical manufacturer, or an eCommerce shop – no one is immune to attacks. IT security consultancy becomes more popular every year as the number of data breaches and orchestrated offenses grows.
Why is cybersecurity consulting in such demand today? The number of attacks grows with the digitalization of all industries and the IoT popularity, which signifies new potential risks. But also because the COVID-19 pandemic resulted in the rapid growth of cybersecurity offenses, protection of which is security DevOps primary responsibility.
For example, 80% of FinTech companies admitted to the increase in cyber attacks. And cloud-based attacks rose by 630% in one year. Phishing attempts increased by 600% too during 2020 and ransomware increased by 148%. All of that shows that software security consulting is as crucial as ever. After all, data breaches cost enterprises $3.92 million on average. At the same time, 40% of IT industry leaders admit that cybersecurity positions are the hardest to fill.
It explains why outsourcing cyber security consulting services is a dashing opportunity.
What Cyber Security Consulting Is About?
Software security consultancy is a growing market that was valued at $156.5 billion worth in 2019. It refers to the firms, companies, and individuals that work in the field of cybersecurity. They help enterprises of all sizes and industries to analyze, test, and update their security systems.
This field concerns everything, from malware up to DDoS attacks and data breaches. Cyber security consulting firms also help with compliance with rules and regulations regarding data protection. These services are essential to update the system, keep up with new threats, and prevent risks. The main focus of excellent cyber security consulting companies is always on a proactive approach and prevention, rather than dealing with consequences. Additionally, technology consultancy services can help businesses optimize their overall IT infrastructure while ensuring security is integrated into every level.
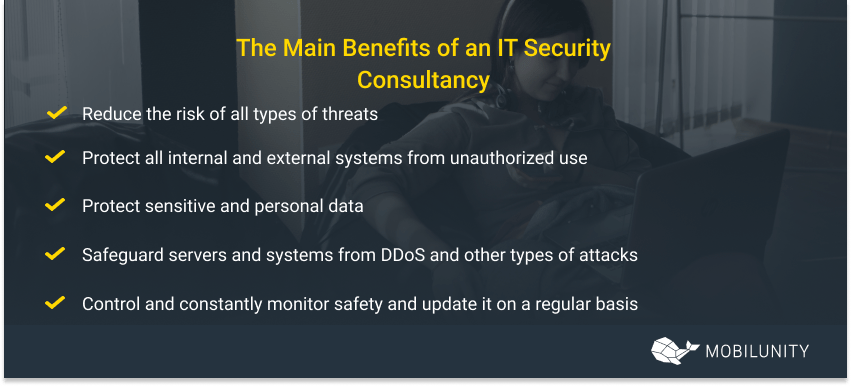
IT security consultancy can help a company to:
- Reduce the risk of all types of threats;
- Protect all internal and external systems from unauthorized use;
- Protect sensitive and personal data;
- Safeguard servers and systems from DDoS and other types of attacks;
- Control and constantly monitor safety and update it on a regular basis
Professionals use security consulting software and the most advanced technologies to implement the best practices to protect a business.
Main Types of Cybersecurity Threats
Generally, all threats can be divided into 5 main categories. These are the types of risks cybersecurity consulting firms and security DevOps have to deal with.
- Malware. This term refers to all kinds of malicious software, like viruses, worms, spyware, etc. They are pretty easy to catch online by clicking the wrong link or simple email attachments. It is one of the most popular threats out there that happens with almost anyone. It can block essential features and data, transmit it in background mode to someone outside, or crash the whole system.
- Phishing. This is a practice web security consulting comes across very often. Basically, phishing means transmitting malware by appearing like a reputable source. For example, one gets an important email that seems to be from their management (there is only one digit difference in the email address that is hard to notice). The person clicks on the attachment or downloads a file and that’s it – the security system is breached.
- Hacking. A cybersecurity consulting firm will help an enterprise protect itself from hacking. Hacking means getting access to the IT system from beyond. It is usually very discreet and has an intention of gaining sensitive information, for example, bank account data or passwords. These are more sophisticated and motivated threats that can cause huge reputation and financial damages.
- DoS/DDoS. Cyber consulting also deals with this threat. In the case of a DoS attack the computer floods the server with a huge amount of UDP and TCP packages that result in server malfunction. The system crashes because it is unable to process this number of requests. DDoS means using several computers from various locations worldwide.
- Man-in-the-Middle.This type of threat happens in times of data transmission between two parties or devices. For example, when someone uses open public Wi-Fi, a hacker can infiltrate and access the transmitted data.
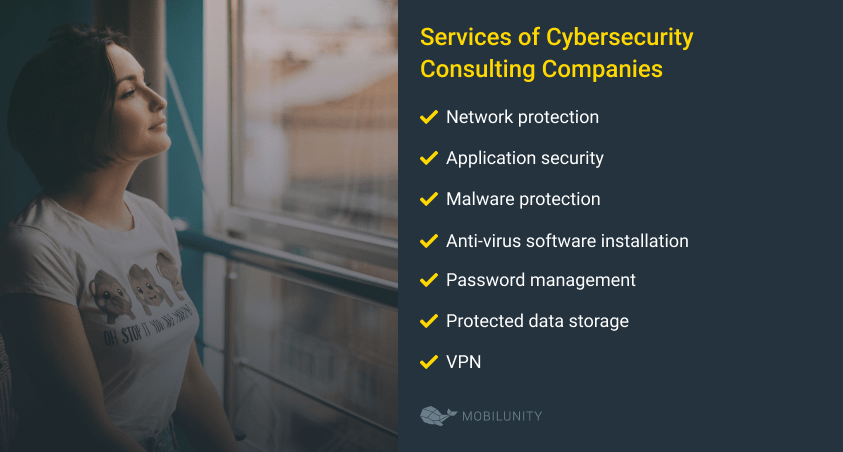
Services of Cybersecurity Consulting Companies
All types of specific services like application security consulting or IT security consulting software cover all matters data protection. Cybersecurity consulting firms offer analysis and assessment of existing protection systems, their testing, and troubleshooting, as well as advice and implementation of more advanced tools. The services may include:
- Network protection, all about internal and external network and its safety from unauthorized access;
- DevOps cloud migration.
- Application security. Web application security consulting deals with making an app protected and inaccessible for any threats.
- Malware protection ensures that any viruses, worms, or any other types of malicious software cannot penetrate or crash the system;
- Anti-virus software installation and adjustments;
- Password management to eliminate any hacker attacks or external access to sensitive data.
- Protected data storage, whether it is in the cloud or on-premise;
- VPN, etc.
Top-notch application security consulting companies also offer customizable solutions that fit perfectly to the particular business and its needs.
The Role and Responsibilities of Cybersecurity Consultant
A cybersecurity consultant is a highly qualified and experienced professional that assesses all security measures, tests them, and finds new ways to make the system more bulletproof. Such professionals proactively work to eliminate any possible risks and weak spots. Consultants also help with the implementation and integration of any new software solutions.
Consultants can work individually, as a permanent team member of a company, or as an employee of a cybersecurity consulting firm. This position requires excellent hard skills and an understanding of the way hackers operate. They need to comprehend the offender’s logic the same way detectives understand the logic of criminals.
Consultants also need communication skills to present their advice and solution to upper management. And they need to always be updated with new threats and new protection technologies. Sometimes consultants can help educate employees on digital hygiene, for example, be cautious of unknown links and files sent via mail.
Professional cybersecurity consultant can help business with:
- Avoiding reputation damage. When it comes to data breaches, it is a hugely damaging situation that can ruin one’s brand. It is essential to put all efforts into eliminating this risk;
- Creating a fully integrated and responsive protection system. It is always better to have a complex solution than several apps that do not correspond with each other.
- Avoiding legal problems and financial risks. In case the company loses clients’ personal information, they can be subject to legal action. They also will be subject to different types of fines.
- Building more trust with customers. Nothing breaks credibility and loyalty like losing customers’ personal information. If an eCommerce shop fails to protect one’s payment info, they will probably never come back to them.
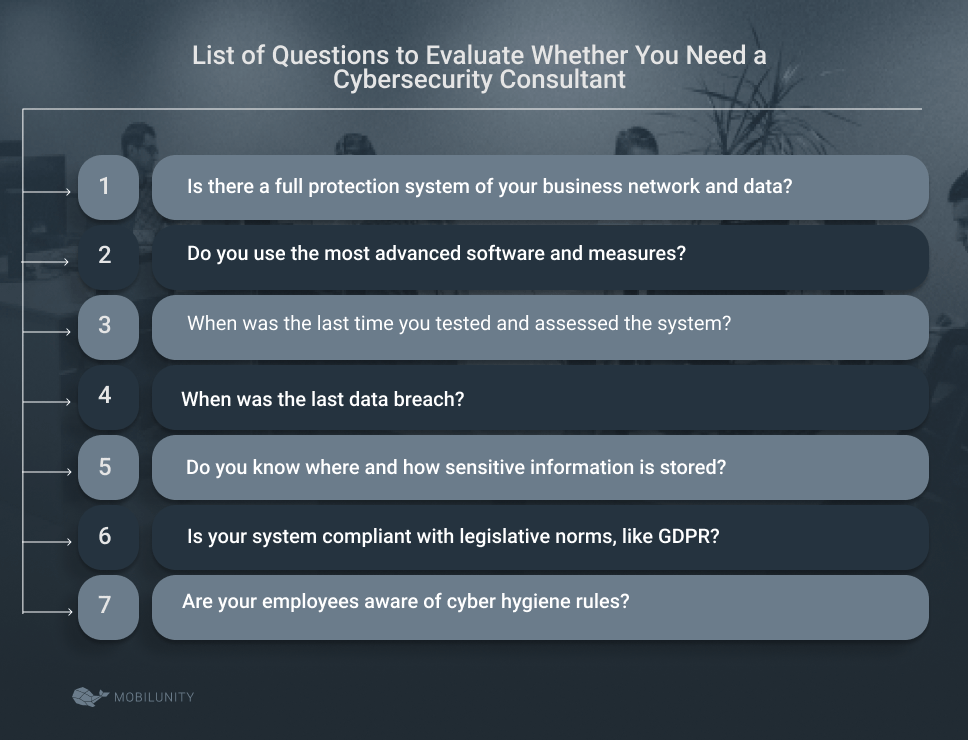
List of Questions to Evaluate Whether You Need a Cybersecurity Consultant
Let’s start with the obvious – cybersecurity consulting services are important and beneficial for any company. It is always better to be safe than sorry. But if you want to be sure, here are the questions to answer before making a decision:
Now, it is time to find a perfect service provider that will help to resolve any issues regarding protection. Consider recommendations, experience, skills set, and type of clients the company or individual has worked with before.
A Perfect Cybersecurity Consulting Firm
Cybersecurity consulting is incredibly important in the modern world where the majority of the data is stored digitally. So a perfect firm will ensure that your company is safe and sound with the most advanced measures and focus on the prevention of any risks. If you want to find a perfect service provider, look at these specific factors:
- Clients’ satisfaction. Nothing speaks more about one’s qualifications than their clients’ reviews. Always look at their portfolio and successful cases where they helped other businesses.
- Recommendations and reputations. You can also contact active clients of the firm to know more about their activities and efficiency. Consider what providers your industry competitors go to.
- Internal reporting system. It is standard practice for an excellent IT company to have a clear and transparent control and management system. It means that they can provide regular reports on what has been done, how much went to specific tasks, etc.
- Excellence in hard skills and ability to predict possible risks. The main trend in digital protection is to prevent rather than act after. The best reaction to any threat is to create a system that will not allow any breaches. A perfect company needs to have forward-thinking and strategy to prevent weak spots and breaches.
Before you settle with one provider, make sure to formulate your requirements and expectations.
Mobilunity – Excellent Ukrainian Vendor
Mobilunity is a credible Ukrainian outstaffing company that has been helping businesses all over the world for more than 10 years. It is quite difficult to find a suitable IT professional at all, not to mention to save some money. We offer access to top-notch Ukrainian talent, whether you are looking for cybersecurity experts, Android application developers or Salesforce CRM consultants.
We have more than 40 satisfied international clients, which we helped with various projects. Mobilunity can find a perfect team for your specific requirements and provide scalability, flexibility, and cost reduction of outsourcing.
Mobilunity helps ICUC (Canada) with social media management, BYG-E (Denmark) with eCommerce platform management and XPLG (Israel) with log analysis platform and data management and security. We know exactly how to find freelance cyber security developers or consultants that will bring your company to a new level of success.
Looking for expert IT security consultants? Contact Mobilunity now!
Disclaimer: All salaries and prices mentioned within the article are approximate numbers based on the research done by our in-house Marketing Research Team. Please use these numbers as a reference for comparison only. Feel free to use the contact form to inquire on the specific cost of the talent according to your vacancy requirements and chosen model of engagement.